We look after the security of the website and the features available through it – sign-up forms, landing pages, chats, etc., and thus, we strive to take the utmost care of your personal data that you enter and share with us when using our website and our services. Therefore, by this Instruction, we will try:
- to inform you about the dangers associated with the use of various products and services to which you have access through the Internet;
- to give you some practical advice which, if followed, would reduce the risk of you being harmed by acquiring and using your personal data for the benefit of malicious persons by committing various types of cybercrime
Access to our website and the forms requiring your personal data to be completed
- Ensure that you access the official website of our company before entering your username and password;
- When accessing our website, especially when using the features available on it that require to enter your personal data, please use only personal smart devices, not shared ones, and it is recommended to use one device, and when using multiple devices – their number should be limited to a minimum. Ensure that the devices you use for this purpose are scanned and protected by appropriate and up-to-date antivirus software;
- Do not enter your personal data in the presence of other people or in public places, and do not use public (open) wireless networks (Wi-Fi);
- Do not use the features of the browser you are using that allow you to auto-complete web addresses that you have started typing. Instead, manually type in our full web address iuvo-group.com;
- Do not add our website in your browser bar (search engine) for your frequently visited sites (Bookmarks, Favorites). Bookmarking your favourite websites makes it easier for malicious persons to find out where and for what purposes you enter your personal data such as: names, telephone numbers, e-mail addresses, user IDs, passwords, etc., and to try to obtain them for abusive purposes;
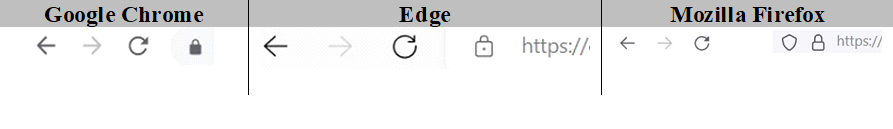
- Always verify that websites are secure. The verification should be carried out in several steps, namely:
– on the left field of the search bar there must be a locked padlock which, depending on your browser, would look like any of the following:
- you need to click on it to open a window containing ‘Connection is secure’ message;
- if you wish, by clicking on ‘Connection is secure’ message, you can also check the details of the website’s security certificate.
Browsers (search engines)
- When using the features of our website(s), never save your username and/or password to access them in your browser;
- Always check whether the browser you are use is still supported by its developer or not, taking into account that, at this time, the support for Internet Explorer has been stopped;
- Update your browser regularly. For your convenience, you can enable automatic update functions;
- Use your browser’s phishing filters;
- Do not install additional toolbars (ASK toolbar, Google toolbar, etc.) because they can be used to distribute malicious software.
Access data
As you know, your username and password are access data. You can learn more about best practices for creating the most secure passwords in the FAQ file.
The two-factor authentication of your accounts
You can learn more about the two-factor authentication of your accounts in our Frequently Asked Questions (FAQ) file.
Technical support of the devices you use
- Ensure that the operating system you use and individual types of software products are as up-to-date as possible. Usually, operating systems and software products available on the market have the option to set up automatic updates. Use this option and always set up your devices to automatically update. If by any chance the operating system and software products installed on your device do not have the option to automatically update, then you can search for the latest versions of them yourself to download and install them. In such case, you should only download the current versions from their manufacturers’ websites. Never download operating systems and software products from messages received via your email or in chat communications with you. Such messages are sent by malicious persons and the request to update operating systems and software products specified in them is fake and intended to access your personal data through malware. By using up-to-date and licensed operating system and software products, you minimize the risk of your personal data being obtained and used by malicious persons;
- Install a firewall on the device that you use to access your various accounts. The function of firewalls is to protect you from malicious persons while you are on the Internet and they can be set up to notify you of attempted attacks by such persons;
- Install a secure and licensed antivirus program developed by an established manufacturer on your device. Its function is to protect your device against various types of viruses through which malicious third parties seek to gain remote access and control over the device you use;
- Do not install or use ‘cracked’ programs downloaded from torrent websites, because this poses a great risk to the security of your device and the data you store on it or enter through it. ‘Cracked’ programs have compromised security and can be used to install malware and Trojan horses on your device;
- Please note that, at this time, Windows XP is not supported by its manufacturer, so we advise you to take action to install an up-to-date operating system to ensure your level of security. We would also like to inform you that the latest version of one of the most widely used operating systems is Windows 11.
Phishing, vishing, smishing and pharming
More details on the meaning of phishing, vishing, smishing and pharming can be found in the Frequently Asked Questions (FAQ) file.
We always remain at your disposal if you have any questions related to our methods and channels of communication with you, including our willingness to render the necessary assistance to you whenever you suspect any abuse against you. You can contact us at the telephone numbers and e-mail below:
Contact telephone numbers: | |
| (BG) + 359 2 493 0108 (UK) +44 20 0333 1998 (EE) + 372 880 7011 (AU) +43 720 883393 (ES) +34 518 889 105 |
 en
en